Protect what matters most with innovative enterprise security solutions
In an increasingly digital landscape, protecting your physical and digital assets is more critical than ever before. With sophisticated phishing and hacking methods targeting your business every day, it's imperative to have robust solutions in place to safeguard the identities of your employees and customers.
Trust in our innovative security solutions to protect what matters most to you. For the last 170+ years, our mission has been to create innovative solutions that safeguard critical industrial sectors.
Our solutions allow you to implement cutting-edge protection, without overly burdening your IT department with complicated deployment and ongoing management demands. With a broad range of solutions to fit every use case, we'll help you find the right solution for your business needs.
Meets diverse enterprise needs

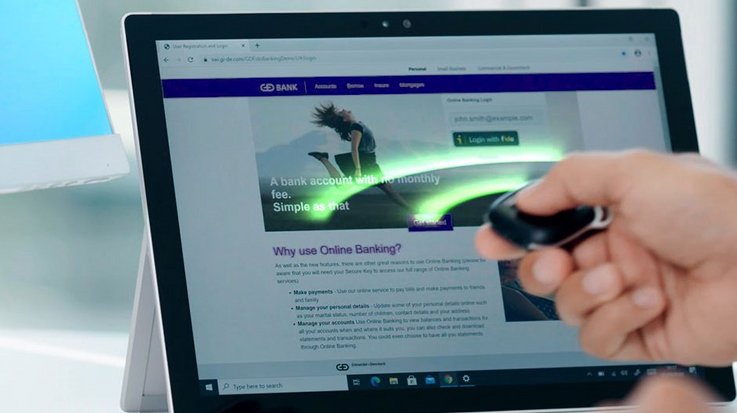
Secure authentication
Ensure your infrastructure remains protected and accessed only by authorized individuals. For example, company laptops that can only be accessed by assigned cryptographic USB fob or key card alongside traditional password or PIN security is present

Mobile payments
Enable security throughout your organization – even in your recreational facilities. Enable a cashless office by allowing employees to pay with their mobile securely in the canteen or other dining facilities.

Secure transactions and signing
Implement secure signing – for example, secure digital contract signing where an audit and signoff trail matters.

Physical access
Secure your physical offices and other locations with identity-based access management – for example restrict access to sensitive parts of your buildings to a subset of your employees.

Encryption
Ensure you and your employees remain protected by encrypting sensitive financial information such as tax documents or pay slips while sending.
Why G+D?
- Unrivaled Security: We've been living and breathing security for over 170 years, and our mission has been to create innovative solutions that safeguard critical industrial sectors.. They all have the highest levels of security, enabled through strong 2FA leveraging encryption & biometric authentication.
- Effortlessly convenient: With frictionless solutions for physical and digital assets that leverage contactless and passwordless ways to authenticate, G+D remains at the forefront of innovation, enabling an ever more convenient customer experience, without compromising on security.
- Caters to a wide range of use cases: Our broad range of offerings (cards, tokens, wristbands, fobs, and software authenticators) meets the need of any business.
- Complete enterprise security: From identity and access issues, fraud management, securing company data to protecting IoT environments, we provide vital building blocks to enable secure and seamless authentication of identities and transactions
- Ease of integration and deployment: Our standard-based solutions ( like PKI, and FIDO) smoothly integrate with your existing infrastructure, offering top-of-the-line authentication to secure any asset, that can scale to meet your individual needs.
- Operations and profit optimization: Leave the heavy lifting to us. We have deployed our security solutions in countless enterprises of all sizes, with all kinds of specific challenges and requirements.
Elevate Your Security with StarSign® Solutions
Say goodbye to the struggle of balancing security and user experience with StarSign® security solutions. Our comprehensive portfolio boasts tried and tested smart and secure products such as smartcards, tokens, key fobs, wristbands, and more, along with scalable services to meet any enterprise's security needs
Your trusted partner for unrivaled security
With G+D as a partner, enterprises and service providers can concentrate on their core business – without having to constantly worry about how to safeguard their physical and digital assets.
Read more about G+DMore insights into enterprise security
Get in touch
If you have any questions about our end-to-end business solutions or about our SecurityTech company, seek expert advice, or want to give us your feedback, our team is here to support you, anytime.