IoT security on the highest level for enterprise and consumer IoT
With every new application of the IoT, device manufacturers and other IoT companies are expected to deliver new and innovative services with better, faster, and sleeker features. And, does it need to be repeated? At the same time, increasingly complex security requirements need to be met. The Internet of Things (IoT) is becoming more present in our daily lives. New applications and developments such as smart cities, autonomous cars, Industrial networks, and Products-as-a-Service (PaaS) capture our attention today. Everywhere, sensors and remote-controlled systems are becoming standard. Ensuring the security of the data transfer is essential, even business critical. All of this is apparent. But the demands on the IoT are often inherently contradictory.
In addition to the call for security, fierce price competition drives the optimization of processes and costs. A seamlessly simple customer experience belies the need for a complex security solution. Secure and convenient-to-use connected devices are indispensable to nurturing consumer trust. Data-sensitive services, such as payment, identification, access, and transport, are essential. Robust, easy-to-manage device security that enriches the customer experience is a strong selling point that can be leveraged to differentiate oneself from the competition.
Mobile operators can securely manage the lifecycle of cellular subscriptions with our proven and future-proof eSIM Management solution that addresses the consumer, enterprise, and IoT markets. But don’t just take our word for it. Our innovative solutions are regularly awarded by renowned IoT security experts.
Sustainability requires trust. For a sustainable IoT, we need to ensure that connected devices and the data they transmit can be trusted.
Dr. Philipp Schulte, CEO of G+D Mobile Security
Empowering IoT security with SIM-based services
The IoT differs according to whether the application is for a consumer or enterprise environment. User-centric consumer applications focus mainly on connected devices with an interface, such as tablets or smartphones. Enterprise IoT applications, on the other hand, run on devices that for the most part are headless, that is, have no monitor or other user interface. They are designed to be data-centric, such as sensors.
Mobile operator SIMs, used to authenticate phones, also enhance IoT security. A SIM serves as a secure root of trust, provisioning and storing digital certificates and credentials. This enables robust device identification, secure server interaction, and data encryption. Existing provisioning infrastructure can be used for cost-effective, safe credential updates on SIMs. Over-the-air additions, including PKI certificates, maintain device identity securely throughout its life.
We offer various SIM-based applications that enhance the security and functionality of IoT use cases and help protect devices and data. Its core services are IoT SAFE, Zero Touch Provisioning, IoT Protect, and SIGNiT®. The platform covers both the backend and SIM software. It enables mobile operators to offer a consolidated toolbox to OEMs and enterprises. They, in turn, are able to manage SIMs and other devices over the entire lifecycle – from manufacturing and activation, to managing subscriptions and policies, all the way to deactivation.
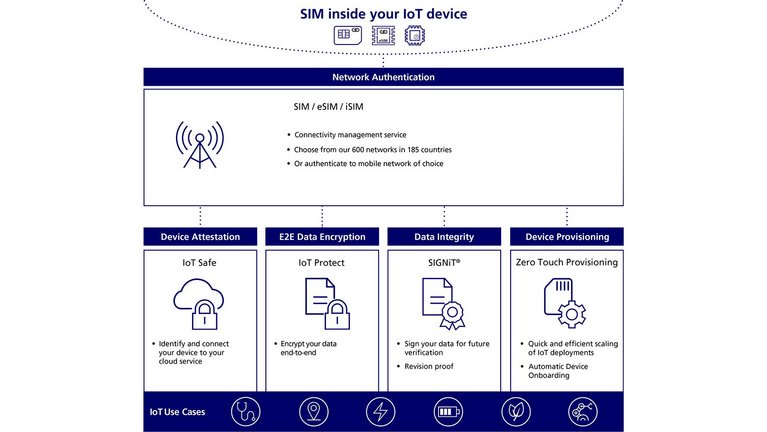
IoT SAFE
Companies build IoT solutions for the marketplace, and these devices connect to cloud platforms. The credentials, however, are mostly stored within the application processor memory. This makes them an easy target for attacks. Our IoT SAFE protects against threats and provides cybersecurity by adding a secure element (a SIM card, eSIM or iSIM) to the IoT device. It is equipped with an applet that assists with the authentication to the cloud provider.
In addition, our offering includes a credential manager that controls and replaces factory credentials. We also offer a device toolkit that provides documentation, which includes the sample code that is used to assist the IoT device developer in securing the communication between the IoT device app and the SIM applet.
Zero Touch Provisioning (ZTP)
For businesses with large fleets of IoT devices in the field, getting these devices up and running can involve a lot of time, effort, and cost. Zero Touch Provisioning is a SIM-based application, for quick, simple device onboarding with no device or platform dependencies.
This innovative tool uses the SIM to negotiate a trusted connection with your API upon first network registration. The ZTP application also requests the device to report its identification, while the location is obtained from the network registration info. This info can be used to provision device settings when the device is switched on.
This enables quick scaling of device deployments and reduces device manufacturing costs as security functions are shifted to the SIM. Large numbers of devices can therefore be deployed simultaneously, enabling organizations to scale their IoT deployments quickly and efficiently.
IoT Protect
The overall functionality of IoT Protect is to provide an end-to-end encryption/decryption mechanism for IoT applications. Information is transmitted securely between the IoT device and the backend, independent of the communication channel (broadband, NB-IoT, Wi-Fi, etc.). Common applications for IoT Protect are those in which the volume of data transferred is low, which is typical for low-end and battery-powered IoT devices.

Juniper Research recognizes G+D’s IoT Protect as a great tool for operators to enable SIM management and IoT lifecycles. The enhanced security for devices in IoT networks is enabled by cryptographic processes of its IoT Protect service. It provides significant protection for IoT applications that can be targets for attacks.
SIGNiT®
SIGNiT® ensures data integrity in multi-party IoT ecosystems by signing every IoT data packet at the source, the sensor, using digital signatures from SIM,eSIM or iSIM. It's an award-winning solution, recognized by Juniper Research for blending secure SIM environments with blockchain technology, facilitating secure, decentralized processes for IoT data.
Commercially proven, it's set to impact diverse sectors, like logistics, agriculture, energy, and automotive. For instance, Lufthansa Industry Solutions relies on SIGNiT® for 100% trustworthy IoT data, incorporating G+D's security tech and a pioneering Ubirch blockchain. This unique combination secures sensor data in an immutable blockchain, setting new standards.

Juniper Research has awarded SIGNiT® from G+D as an innovative solution to combine secure and proven SIM environments with blockchain technology. It allows to easily digitalize and secure processes in a decentralized ecosystem while providing IoT users with comprehensive and robust security for data generated by IoT devices. The solution has already been successfully implemented in commercial environments, and Juniper Research expects SIGNiT® to have further positive impacts in other IoT sectors, such as logistics, agriculture, energy and the automotive industry.
Downloads
Info brochure

SIGNiT® uses blockchain technology to ensure data integrity
SIGNiT® provides data reliability in an IoT ecosystem where multiple parties must rely of the data. It ensures there is no possibility of data manipulation or deletion by storing digital signatures of the data in a public blockchain. Read more about our solution in our info brochure.
Case study
Food tracking with BayWa Global Produce
To ensure the best quality of apples and the end-to-end tracking of the fruit transport from Antwerp in Belgium to Kressbronn in Germany, BayWa Global Produce has chosen to implement a solution along with G+D.
Case study

Data integrity for the logistics industry
Lufthansa Industry Solutions (LHIND) offers its customers secure, blockchain-enabled damage detection powered by our SIGNiT® solution. In our case study, you'll learn how Lufthansa ensures the integrity of IoT data in its logistics platform.
Network Security
Securing the IoT network is crucial to protect interconnected devices, from smart home gadgets to industrial systems. Robust security is not merely a feature but a necessity for maintaining trust, resilience, and innovation in the rapidly evolving IoT landscape. We offer network-based security to fortify and safeguard your digital infrastructure.
Site-to-Site VPN
Sending valuable information over the public internet can be risky. IoT devices often cannot support basic security features such as two-factor authentication, firewalls or software patches and updates.
Our Site-to-Site VPN (Virtual Private Network) operates from each of our network Points of Presence (PoPs), to help keep your IoT solutions and your data safe. Our IPsec VPN disguises your network to create a barrier to entry for malicious actors, providing peace-of-mind while using the public internet.
More insights into IoT security
We connect the IoT and provide security for data and devices
G+D solutions connect, manage, and secure IoT. We have been offering safe, robust products for enterprises operating networked devices in the world of IoT since the start.
Get in touch
If you have any questions about our end-to-end business solutions or about our SecurityTech company, seek expert advice, or want to give us your feedback, our team is here to support you, anytime.